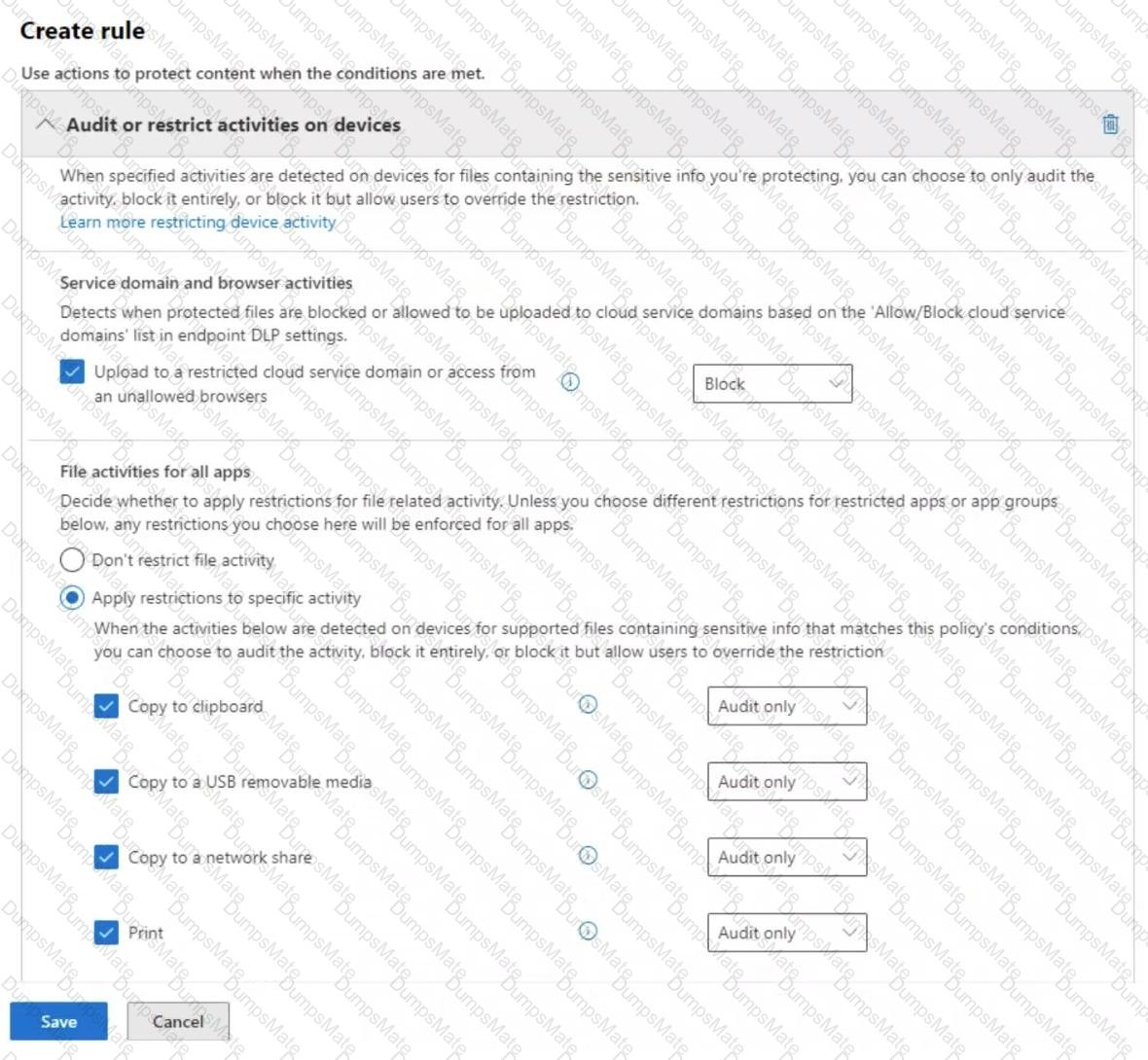
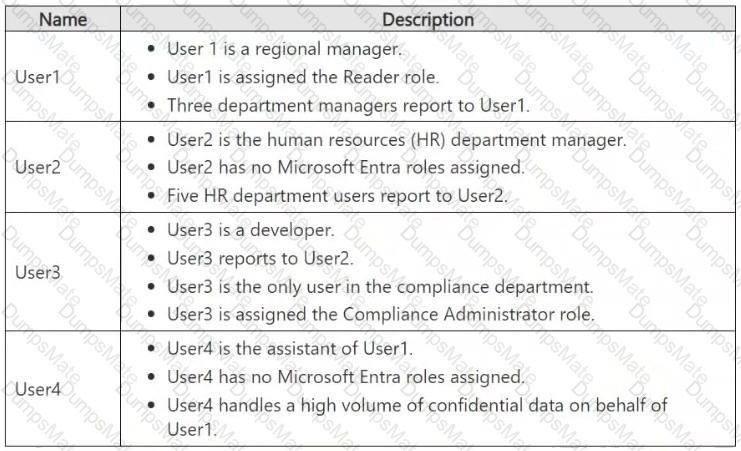
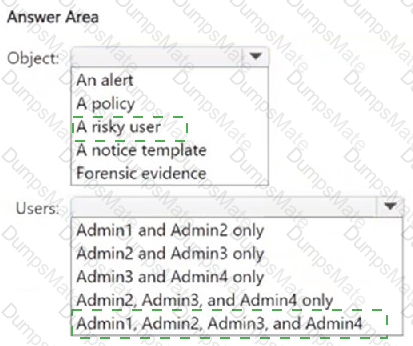
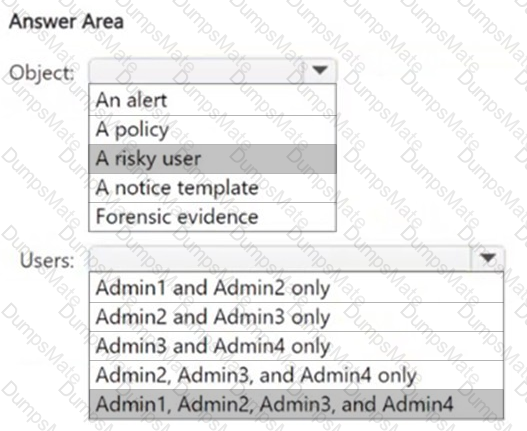
Microsoft Purview Insider Risk Management flags high-impact users based on various risk factors, including role, access to confidential data, and influence within an organization. Let's analyze each user:
User1 (Regional Manager, assigned Reader role, manages department managers)
Risk Factors:
● Holds a managerial position (regional manager).
● Manages multiple department managers, indicating organizational influence.
● Access to critical business information.
Flagged? -Yes (Managerial role and access to confidential data).
User2 (HR department manager, no Microsoft Entra roles, manages HR department users)
Risk Factors:
● Manages HR department users, meaning they likely handle sensitive employee data.
● HR roles are often considered high-risk due to access to personal and payroll data.
Flagged? -Yes (HR role and access to sensitive employee data).
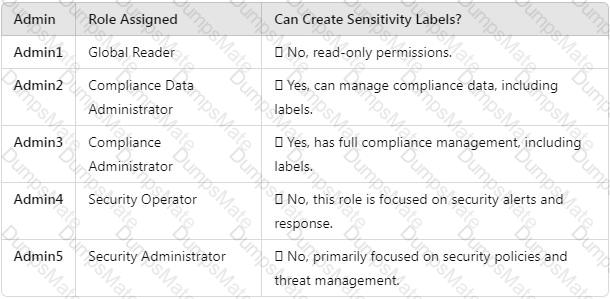
User3 (Developer, reports to User2, only user in compliance, assigned Compliance Administrator role)
Risk Factors:
● Compliance Administrator role grants access to sensitive security and regulatory data.
● Only person in the compliance department, meaning they hold a critical role.
● Potentially high impact on compliance and security settings.
Flagged? -Yes (Privileged Compliance Administrator role).
User4 (Assistant to User1, no Entra roles, handles confidential data on behalf of User1)
Risk Factors:
● Handles a high volume of confidential data on behalf of a regional manager.
● Assistants with access to sensitive data are considered insider risk candidates.
Flagged? -Yes (High access to sensitive information).
Since all four users fit high-impact criteria (managerial roles, privileged compliance access, handling sensitive data), Microsoft Purview Insider Risk Management will flag all of them.



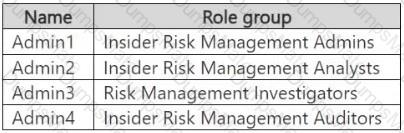
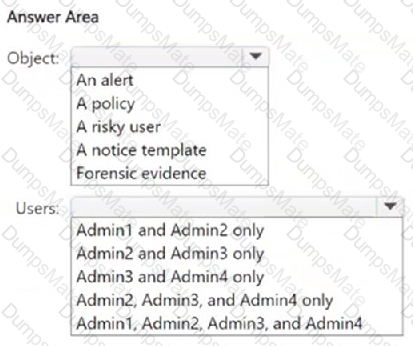
 A screenshot of a computer
AI-generated content may be incorrect.
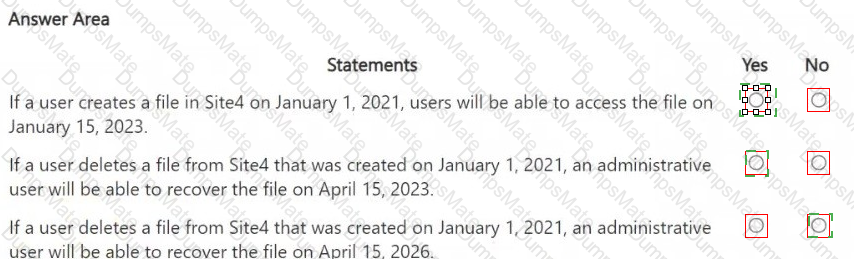
A screenshot of a computer
AI-generated content may be incorrect.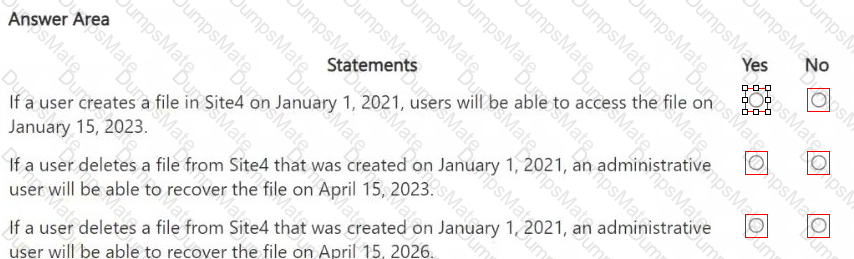
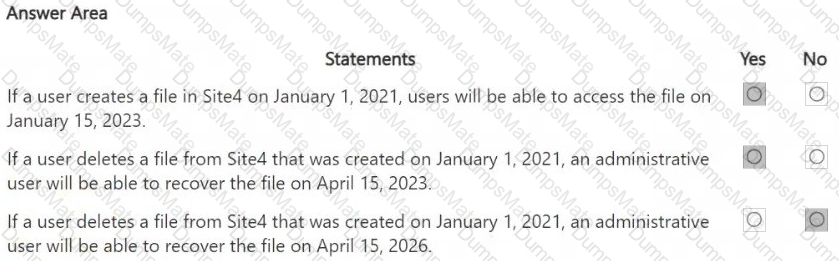 A white paper with black text
AI-generated content may be incorrect.
A white paper with black text
AI-generated content may be incorrect.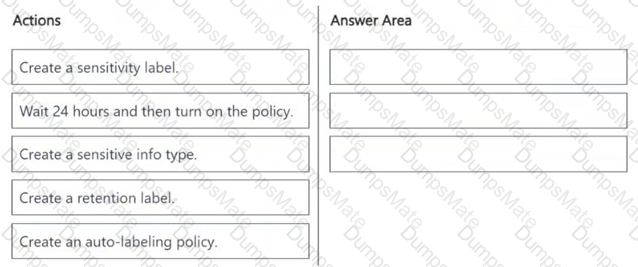
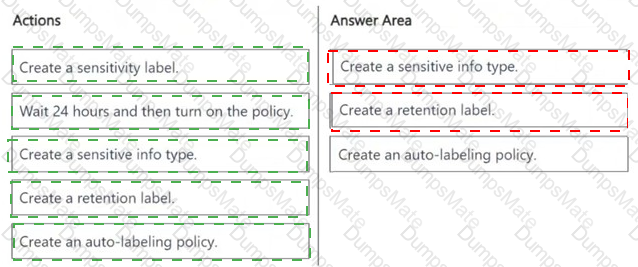
 A screenshot of a questionnaire
AI-generated content may be incorrect.
A screenshot of a questionnaire
AI-generated content may be incorrect.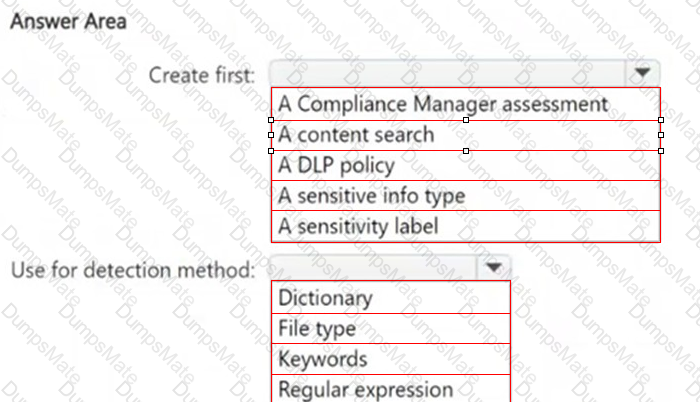
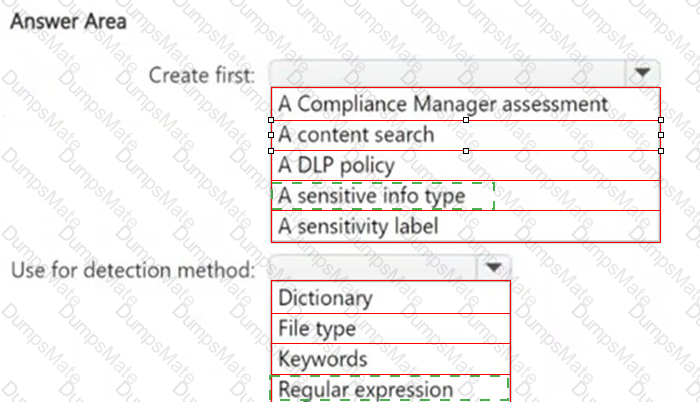
 A screenshot of a computer
AI-generated content may be incorrect.
A screenshot of a computer
AI-generated content may be incorrect.