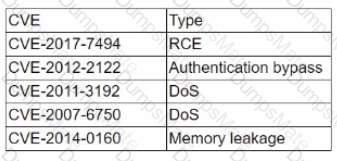
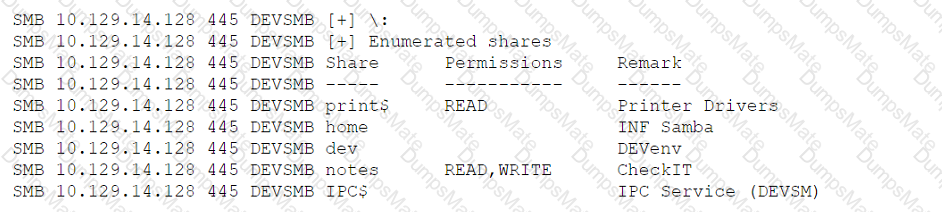
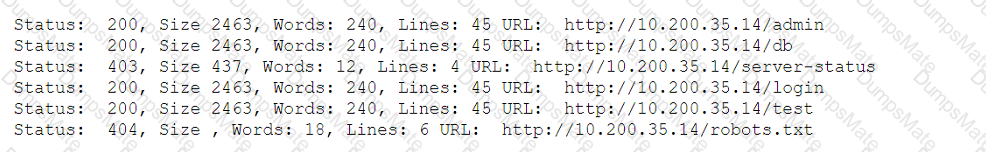
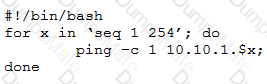
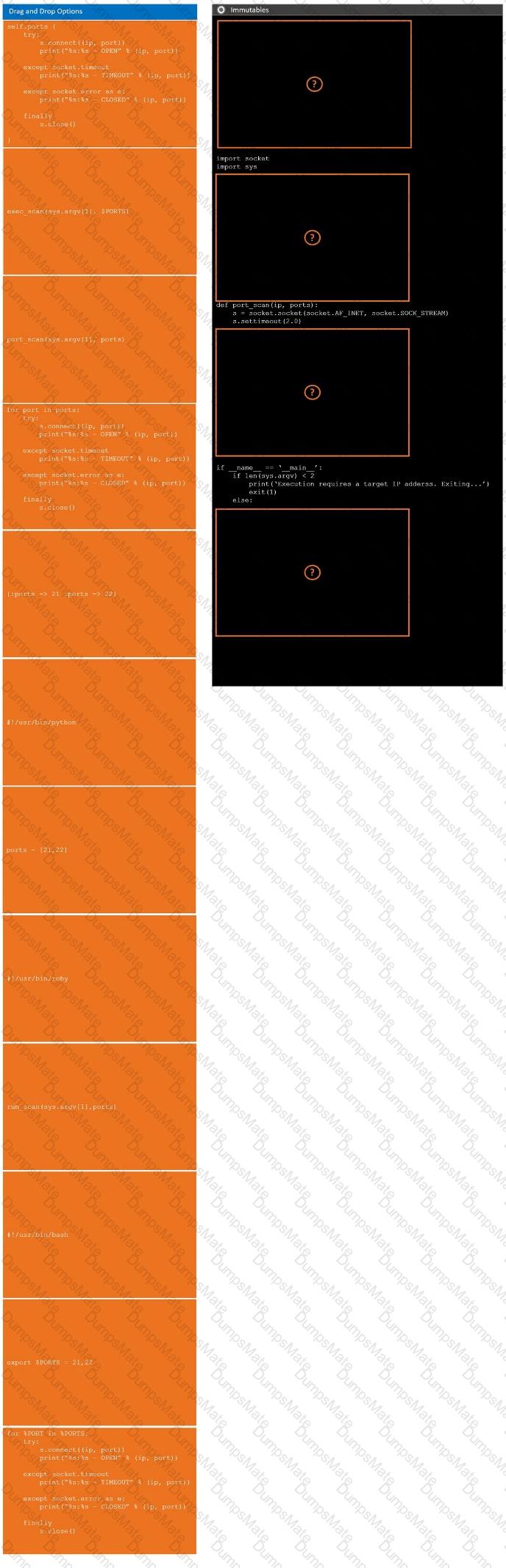
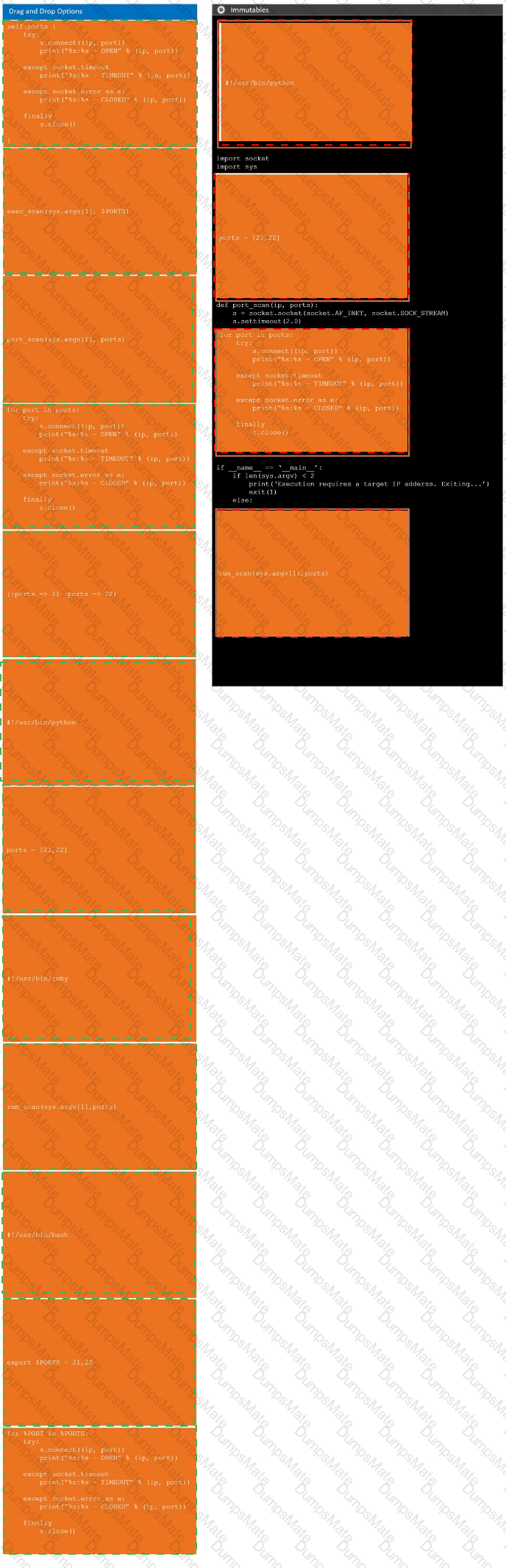
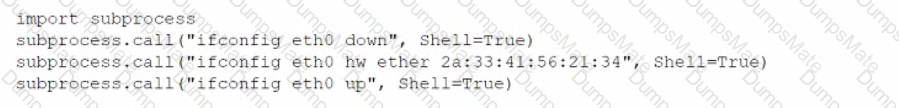
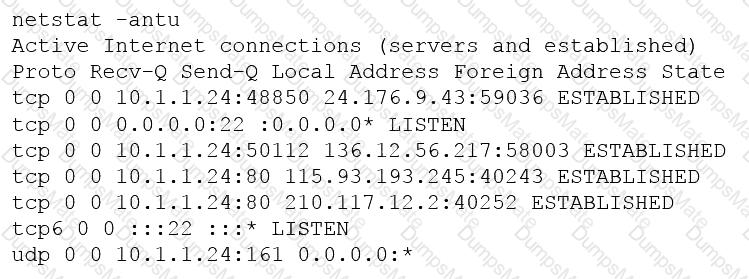
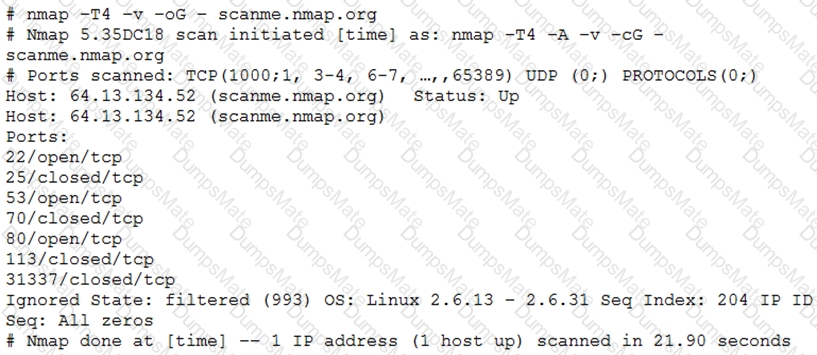
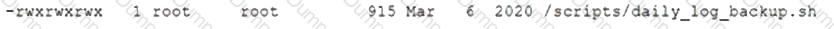A penetration tester developed the following script to be used during an engagement:
#!/usr/bin/python
import socket, sys
ports = [21, 22, 23, 25, 80, 139, 443, 445, 3306, 3389]
if len(sys.argv) > 1:
target = socket.gethostbyname (sys. argv [0])
else:
print ("Few arguments.")
print ("Syntax: python {} ". format (sys. argv [0]))
sys.exit ()
try:
for port in ports:
s = socket. socket (socket. AF_INET, socket. SOCK_STREAM)
s.settimeout (2)
result = s.connect_ex ((target, port) )
if result == 0:
print ("Port {} is opened". format (port) )
except KeyboardInterrupt:
print ("\nExiting ... ")
sys.exit ()
However, when the penetration tester ran the script, the tester received the following message:
socket.gaierror: [Errno -2] Name or service not known
Which of the following changes should the penetration tester implement to fix the script?