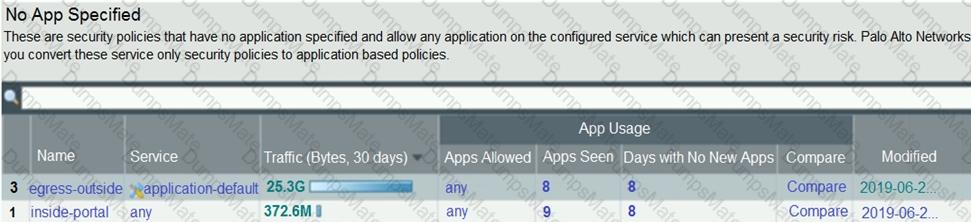
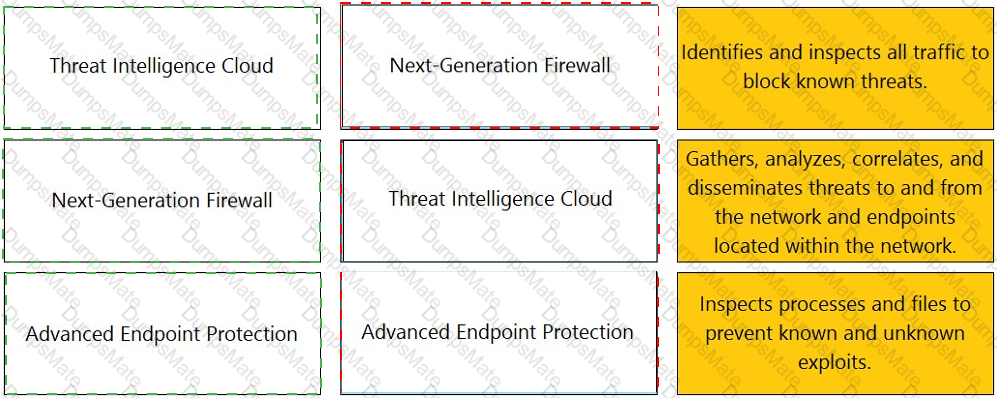
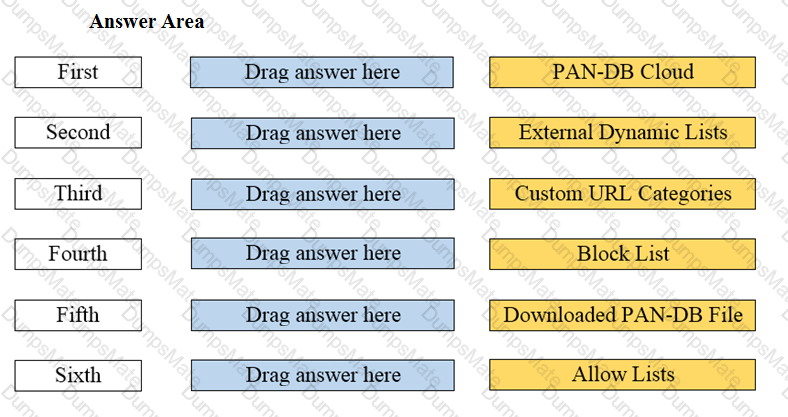
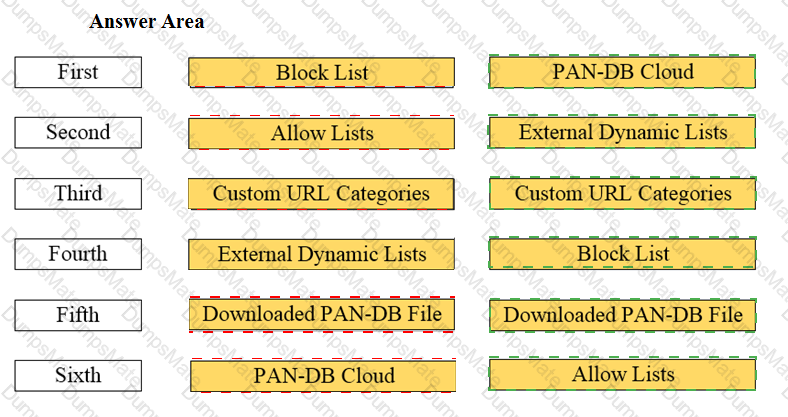
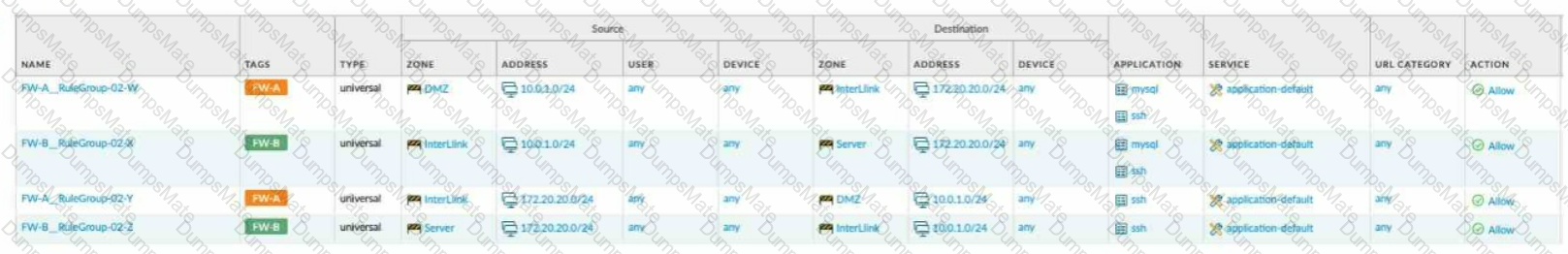
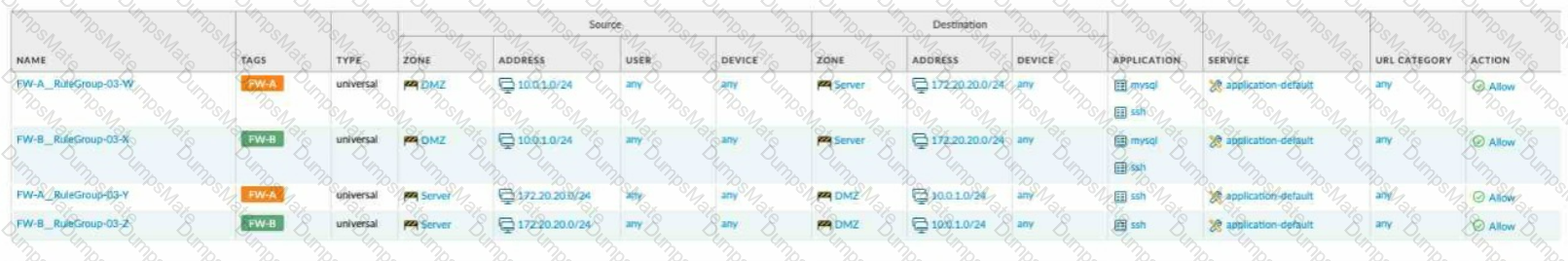
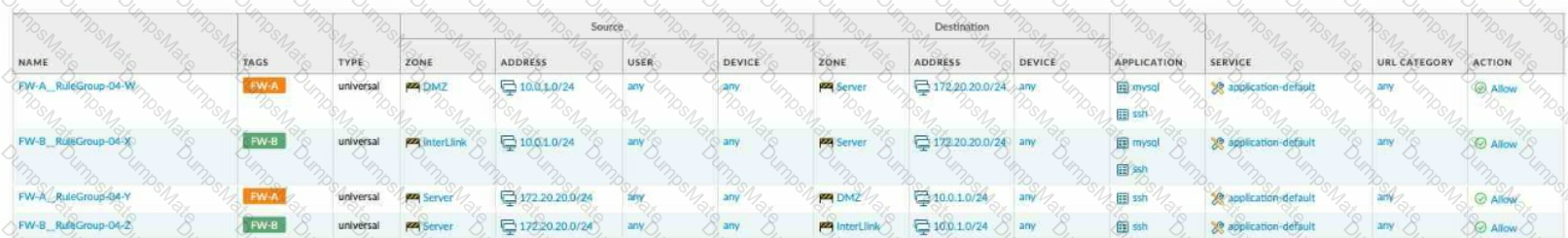
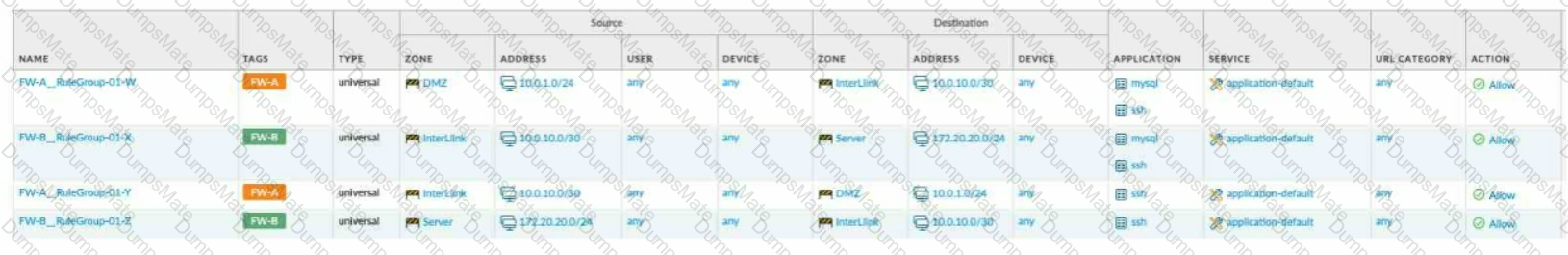
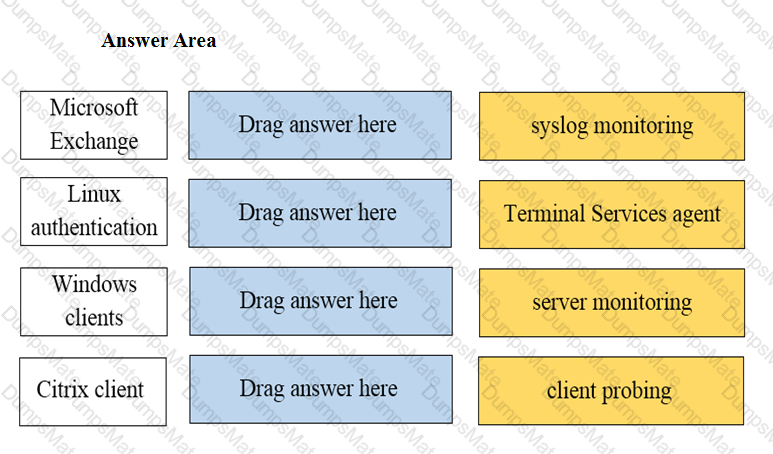
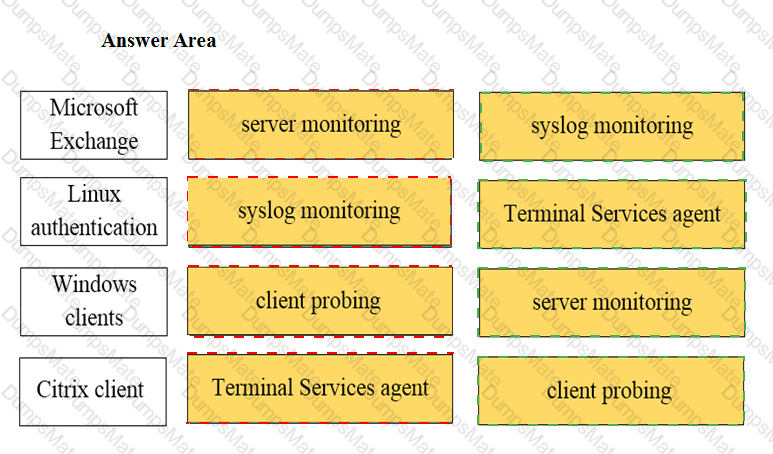
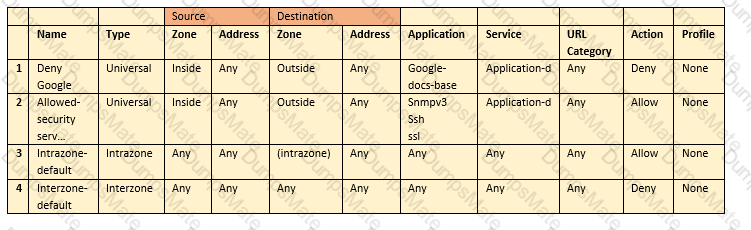
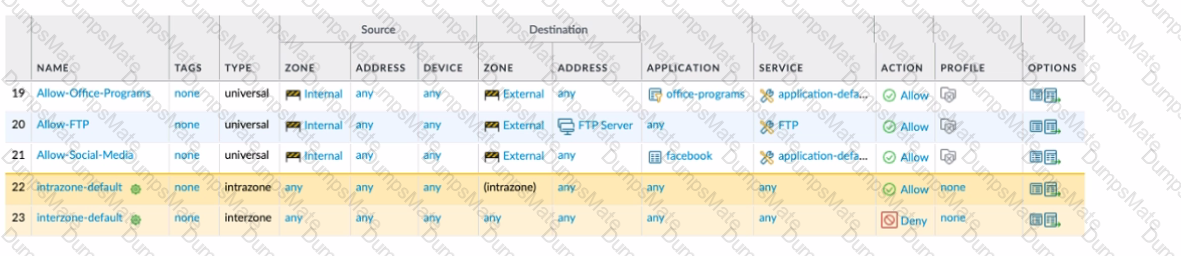
Explanation: The application characteristics can be found in three places on the PAN-OS interface: Objects tab > Application Filters, Objects tab > Application Groups, and Objects tab > Applications. These places allow you to view and manage the applications and application groups that are used in your Security policy rules. You can also create custom applications and application filters based on various attributes, such as category, subcategory, technology, risk, and behavior1. Some of the characteristics of these places are:
Objects tab > Application Filters: An application filter is a dynamic object that groups applications based on specific criteria. You can use an application filter to match multiple applications in a Security policy rule without having to list them individually. For example, you can create an application filter that includes all applications that have a high risk level or use peer-to-peer technology.
Objects tab > Application Groups: An application group is a static object that groups applications based on your custom requirements. You can use an application group to match multiple applications in a Security policy rule without having to list them individually. For example, you can create an application group that includes all applications that are related to a specific business function or project.
Objects tab > Applications: An application is an object that identifies and classifies network traffic based on App-ID, which is a technology that uses multiple attributes to identify applications. You can use an application to match a specific application in a Security policy rule and control its access and behavior. For example, you can use an application to allow web browsing but block file sharing or social networking.
References: Objects, [Application Filters], [Application Groups], [Applications], Updated Certifications for PAN-OS 10.1, Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0) or [Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0)].