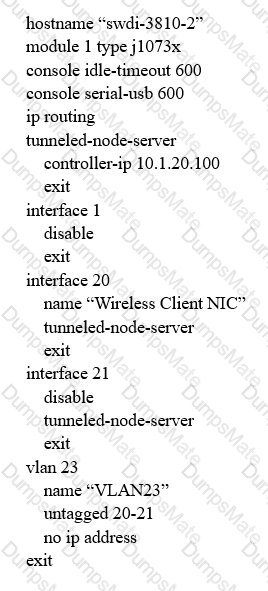
An administrator manages an Aruba wireless network. Users authenticate to the wireless network using PEAP, where their credentials are validated by the controller’s local database. The company purchases Android tablets to use with an inventory tracking system. The administrator notices that many of the users of these devices use their normal username and password to authenticate, which allows the tablet to access all resources that the user can access from their wireless computers. This is a security violation.
Which Aruba Mobility Controller (MC) feature should the administrator configure to restrict tablet access to a web portal for authentication, where an appropriate post-authentication policy can be applied to these tablets?