Understanding HTTP/1.1 Response Structure
???? What is an HTTP Response?
The response is sent from the server to the client after processing an HTTP request.
The structure follows a standardized format:
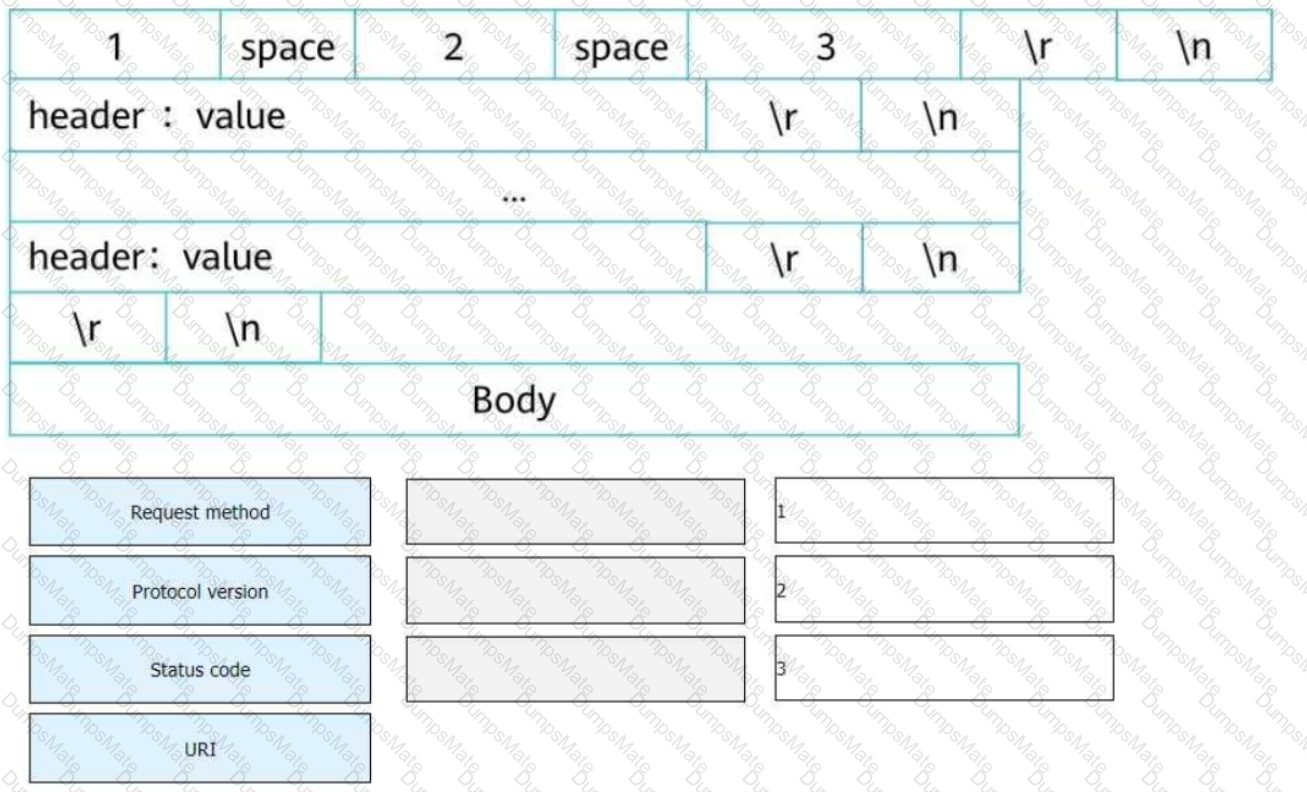
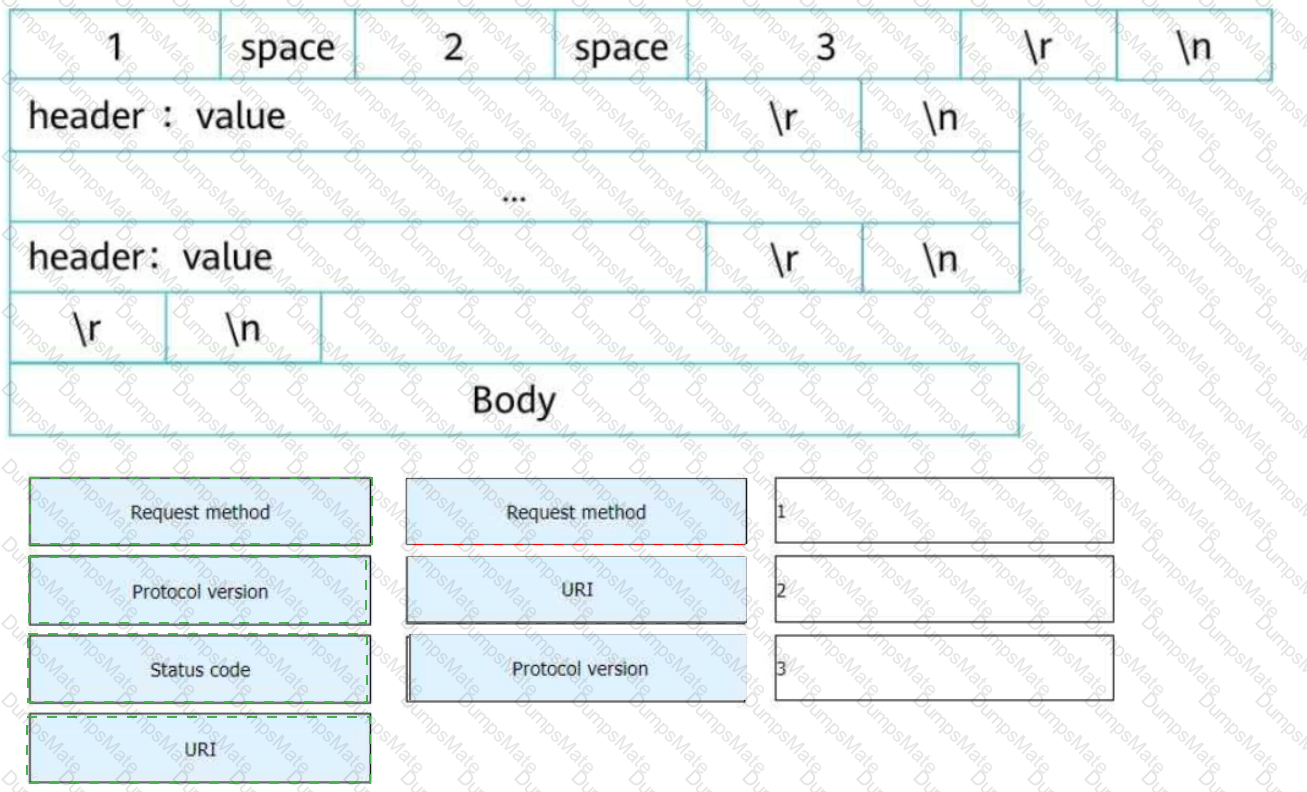
Elements of an HTTP/1.1 Response:
✅ A. Status Line → Contains protocol version, status code, and reason phrase.✅ B. Response Body → Contains HTML, JSON, XML, or other content.✅ C. Response Header → Provides metadata about the response (e.g., Content-Type, Server).✅ D. Empty Line → A blank line separates headers from the response body.
Example of an HTTP/1.1 Response:
HTTP/1.1 200 OK
Date: Sat, 08 Mar 2025 14:00:00 GMT
Server: Apache/2.4.41 (Ubuntu)
Content-Type: text/html; charset=UTF-8
Welcome to Huawei Datacom
Why is the Answer A, B, C, D?
✅ An HTTP response includes a status line, headers, an empty line, and a response body.
Real-World Application:
Web Application Debugging: Helps developers analyze server responses.
API Security: Validates response headers to prevent injection attacks.
✅ Reference: Huawei HCIE-Datacom Guide – HTTP Protocol and Response Headers




 A screenshot of a computer
AI-generated content may be incorrect.
A screenshot of a computer
AI-generated content may be incorrect.
