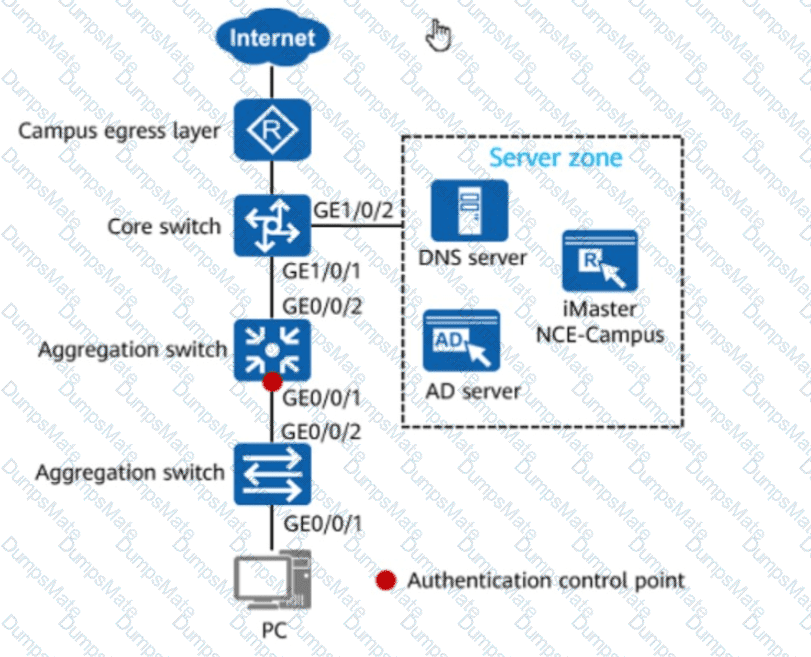
Understanding 802.1X Authentication in Wired Networks:
802.1X is a port-based network access control (PNAC) protocolthat requires aLayer 2 connectionbetween thesupplicant (PC), the authenticator (switch), and the authentication server (e.g., RADIUS server).
In wired networks,802.1X authentication occurs at the Ethernet switch (Layer 2 device), which enforces authenticationbefore allowing network access.
Why Must the Network Be Layer 2?
802.1X authentication operates at Layer 2 (Data Link Layer) before any IP-based communication (Layer 3) occurs.
If the authentication device and user terminal were on different Layer 3 networks, the authentication packets (EAPOL - Extensible Authentication Protocol Over LAN)would not be forwarded.
In the figure, the authentication control point is at theaggregation switch, which means thePC and switch must be in the same Layer 2 domain.
Components of 802.1X Authentication in the Figure:
Supplicant (PC)→ The device requesting network access.
Authenticator (Aggregation Switch)→ The switch controlling access to the network based on authentication results.
Authentication Server (iMaster NCE-Campus & AD Server)→ Verifies user credentials and grants or denies access.
Layer 2 Connectivity Requirement→ ThePC must be in the same Layer 2 networkas theAuthenticatorto communicate via EAPOL.
Why "TRUE" is the Correct Answer:
802.1X authentication is performed before IP addresses are assigned, meaning it can only operate in a Layer 2 network.
EAPOL (Extensible Authentication Protocol Over LAN) messages are not routableand must stay within a single Layer 2 broadcast domain.
In enterprise networks,VLAN-based 802.1X authentication is often used, where authenticated users are assigned to a specific VLAN.
HCIP-Security References:
Huawei HCIP-Security Guide→ 802.1X Authentication in Enterprise Networks
Huawei iMaster NCE-Campus Documentation→ Authentication Control and NAC Deployment
IEEE 802.1X Standard Documentation→ Layer 2 Network Authentication