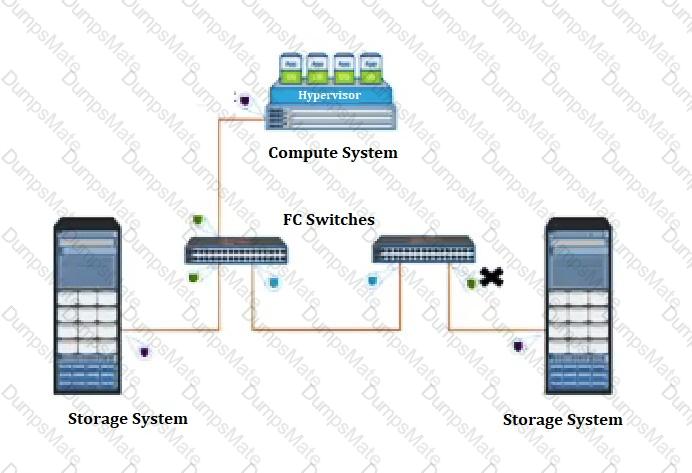
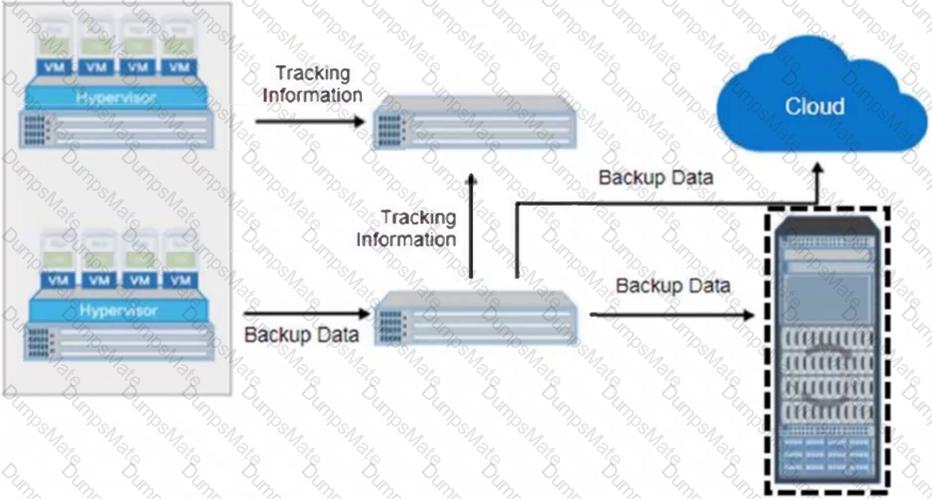
Explanation: Organizations must store, protect, and manage their data in order to comply with the various laws and regulations governing the use and storage of data, such as GDPR and CCPA. By properly managing their data, organizations can ensure that they are compliant with these regulations and avoid potential penalties. Additionally, by storing, protecting, and managing their data, organizations can ensure that their data is secure and protected from malicious actors.
it is important for organizations to store, protect and manage their data because data is a valuable asset that can drive business growth, innovation, and competitive advantage. Data can also be subject to various risks such as loss, corruption, theft, unauthorized access, and compliance violations.
One of the reasons why it is important for organizations to store, protect and manage their data is to meet the requirements of legal and data governance regulations1. This means that organizations should comply with the laws and policies that govern howdata should be collected, stored, processed, shared, and disposed of. Data governance also ensures that data quality, security, privacy, and ethics are maintained throughout the data lifecycle.