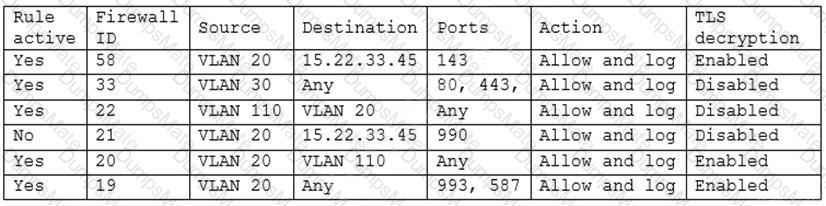
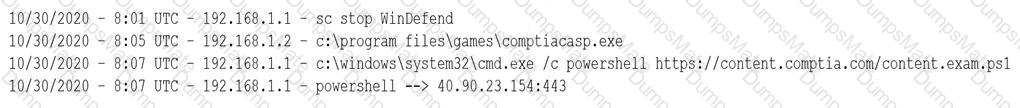
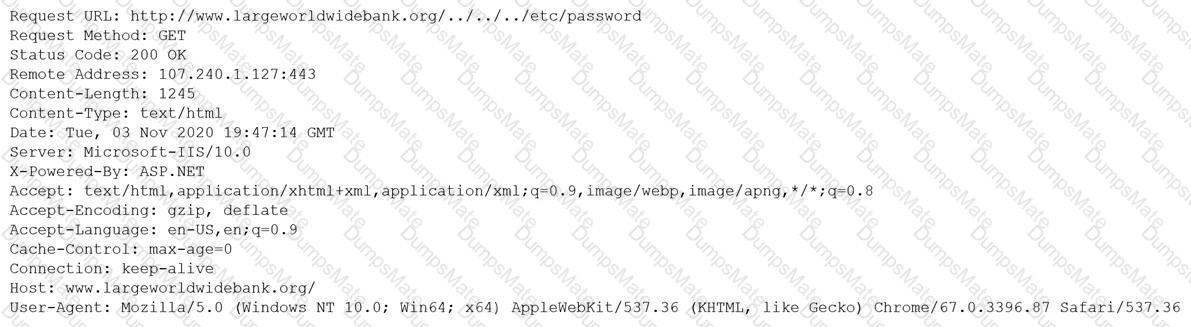
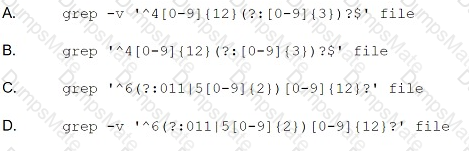
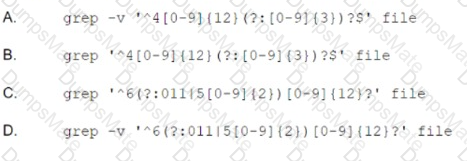
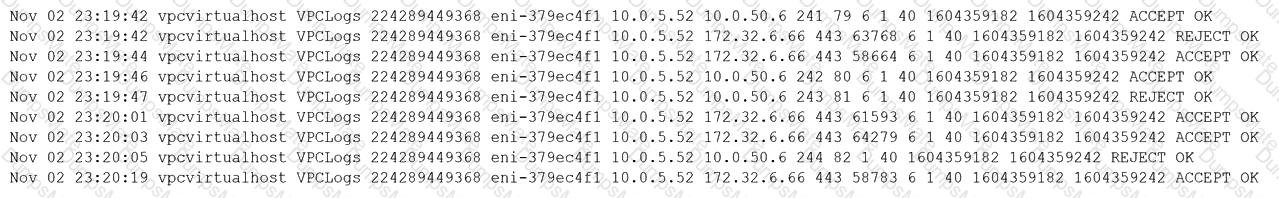
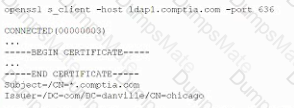
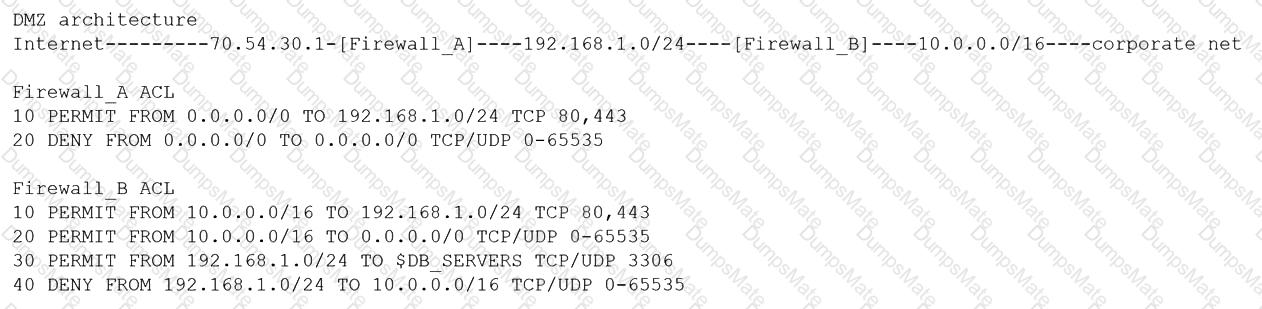
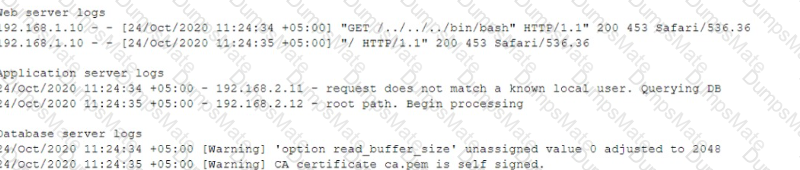
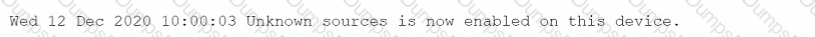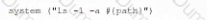A company wants to implement a new website that will be accessible via browsers with no mobile applications available. The new website will allow customers to submit sensitive medical information securely and receive online medical advice. The company already has multiple other websites where it provides various public health data and information. The new website must implement the following:
• The highest form Of web identity validation
• Encryption of all web transactions
• The strongest encryption in-transit
• Logical separation based on data sensitivity
Other things that should be considered include:
• The company operates multiple other websites that use encryption.
• The company wants to minimize total expenditure.
• The company wants to minimize complexity
Which of the following should the company implement on its new website? (Select TWO).