Explanation: In a load balanced Horizon POD with three Connection Servers, there are 450 active Blast sessions connected. If one of these Connection Servers runs into an unplanned outage, only the active sessions from the failed Connection Server are disconnected, because HTTPS Secure Tunnel is disabled. This means that the other two Connection Servers can still handle the remaining sessions without interruption.
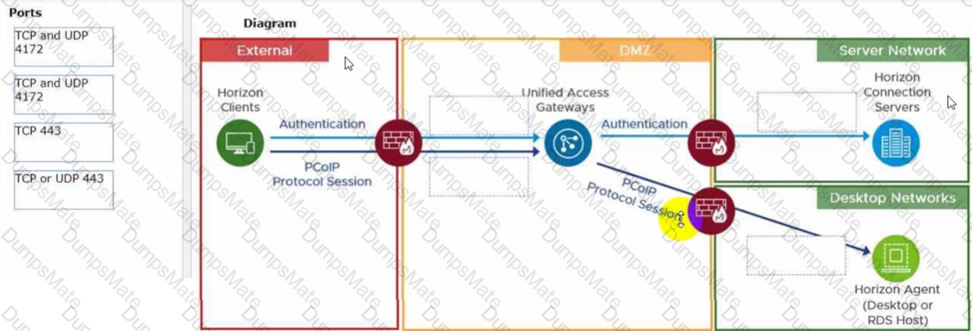
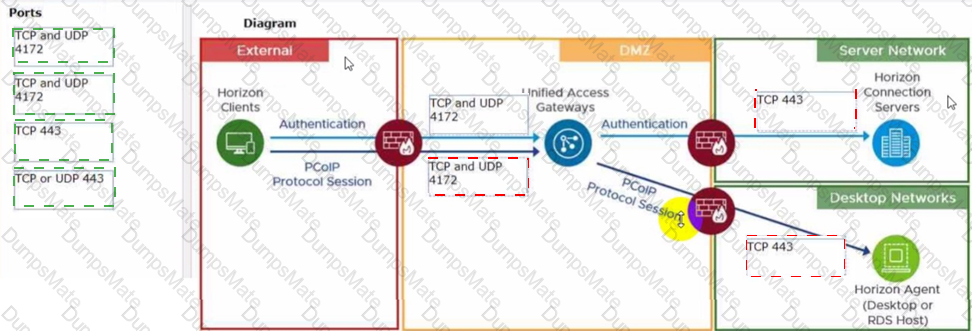
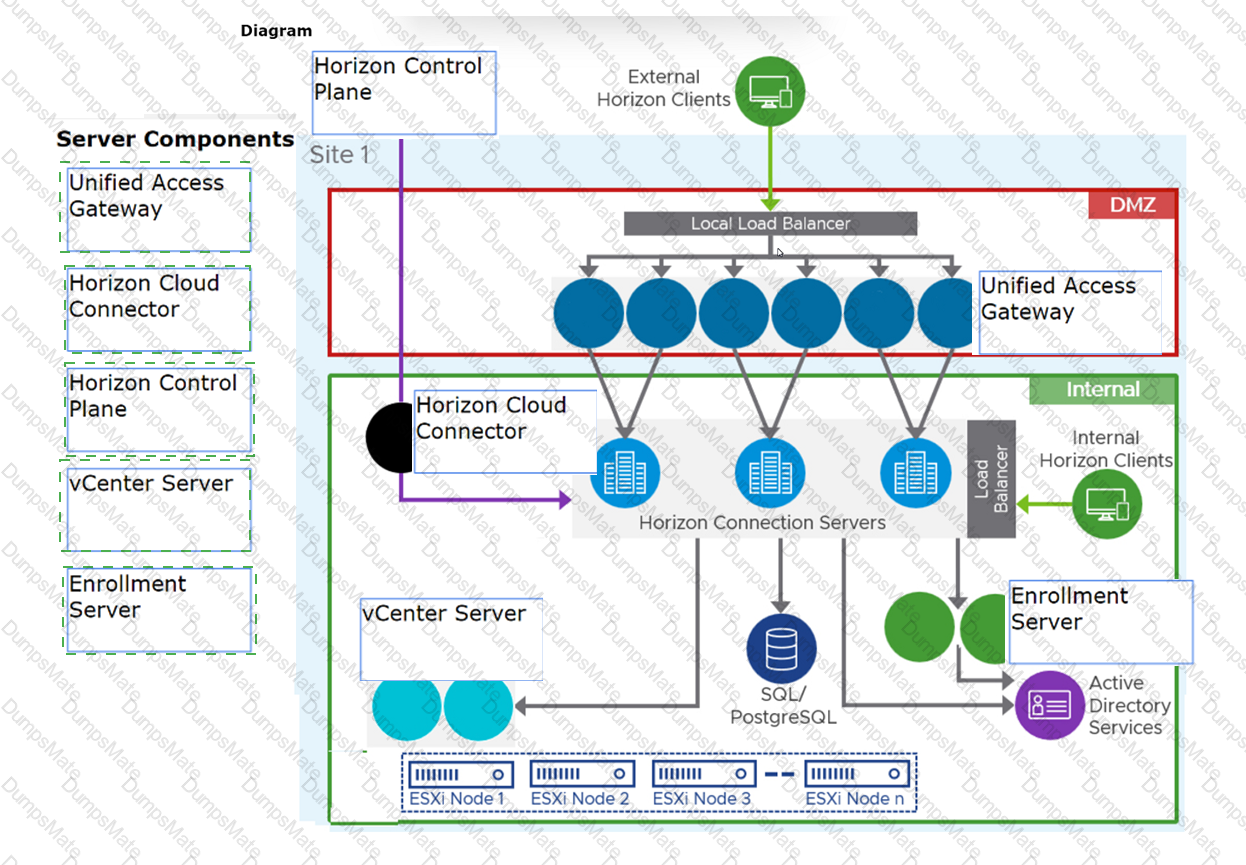
The HTTPS Secure Tunnel is a feature that allows Horizon Client devices to establish secure connections to virtual desktops and applications through the Connection Server. When this feature is enabled, all the display protocol traffic is tunneled through the Connection Server, which acts as a proxy between the client and the desktop. This increases the security and simplifies the network configuration, but also adds some overhead and dependency on the Connection Server availability1.
When this feature is disabled, the Horizon Client devices connect directly to the desktops using their IP addresses or hostnames, bypassing the Connection Server. This reduces the load and dependency on the Connection Server, but also requires more network configuration and firewall rules to allow direct access to the desktops2.
The Blast Secure Gateway is a similar feature that allows Horizon Client devices to establish secure connections to virtual desktops and applications using the Blast Extreme protocol through the Connection Server. When this feature is enabled, the Blast Extreme traffic is tunneled through the Connection Server, which acts as a gateway between the client and the desktop. When this feature is disabled, the Horizon Client devices connect directly to the desktops using Blast Extreme3.
In this scenario, both HTTPS Secure Tunnel and Blast Secure Gateway are disabled, which means that the Horizon Client devices connect directly to the desktops using Blast Extreme. Therefore, if one of the Connection Servers fails, only the sessions that were authenticated by that Connection Server are affected. The other sessions can continue without interruption, as long as they can reach their desktops directly4.
The other options are not correct for this scenario:
- All 450 active sessions are disconnected, and have to re-connect again by the end-user. This would be true if HTTPS Secure Tunnel or Blast Secure Gateway were enabled, and all the display protocol traffic was tunneled through the Connection Server. In that case, any failure of a Connection Server would disconnect all the sessions that were using it as a proxy5.
- All active sessions will stay connected, because HTTPS Secure Tunnel and Blast Secure Gateway are disabled. This would be true if there was no dependency on the Connection Server after authentication. However, even with HTTPS Secure Tunnel and Blast Secure Gateway disabled, there is still some communication between the Horizon Client and the Connection Server for session management and heartbeat monitoring. If a Connection Server fails, these communications are lost and the sessions are terminated.
- All 450 active session are logged off immediately. This would be true if there was a global setting in Horizon Console to log off users when a Connection Server fails. However, there is no such setting in Horizon Console. The default behavior is to disconnect users when a Connection Server fails, not log them off.
References:
- Configuring HTTPS Secure Tunnel
- Configuring Network Ports for Direct Connections
- Configuring Blast Secure Gateway
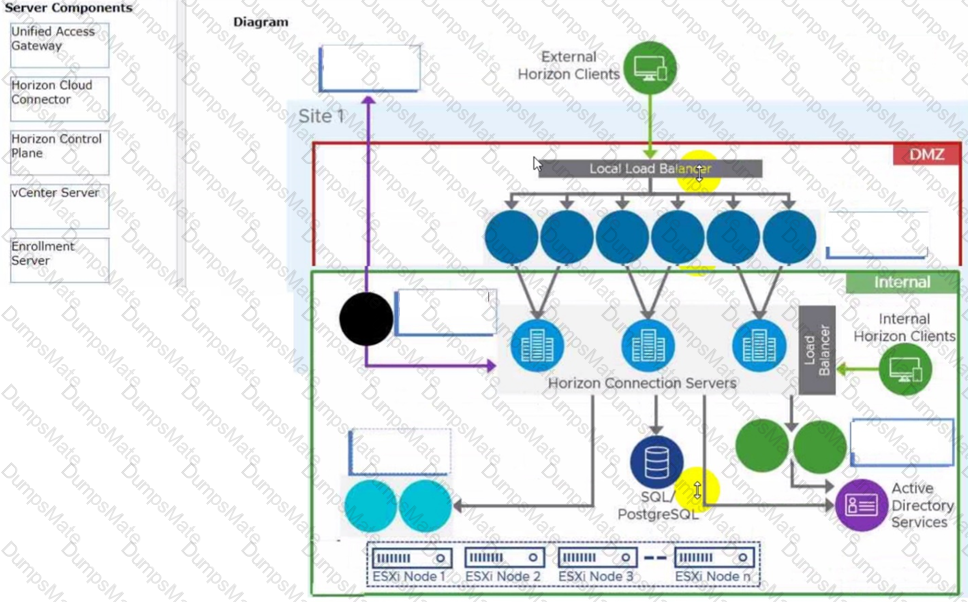
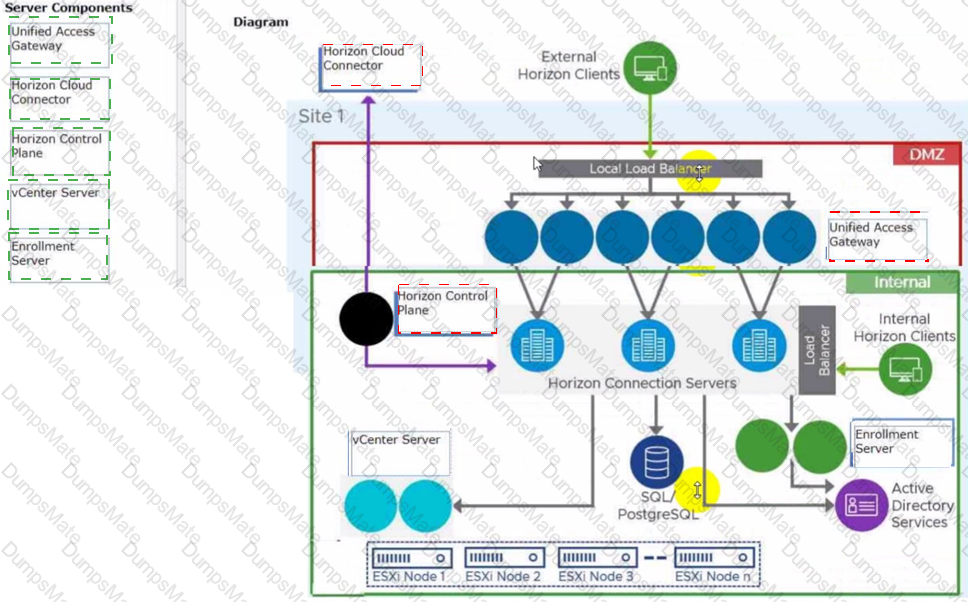
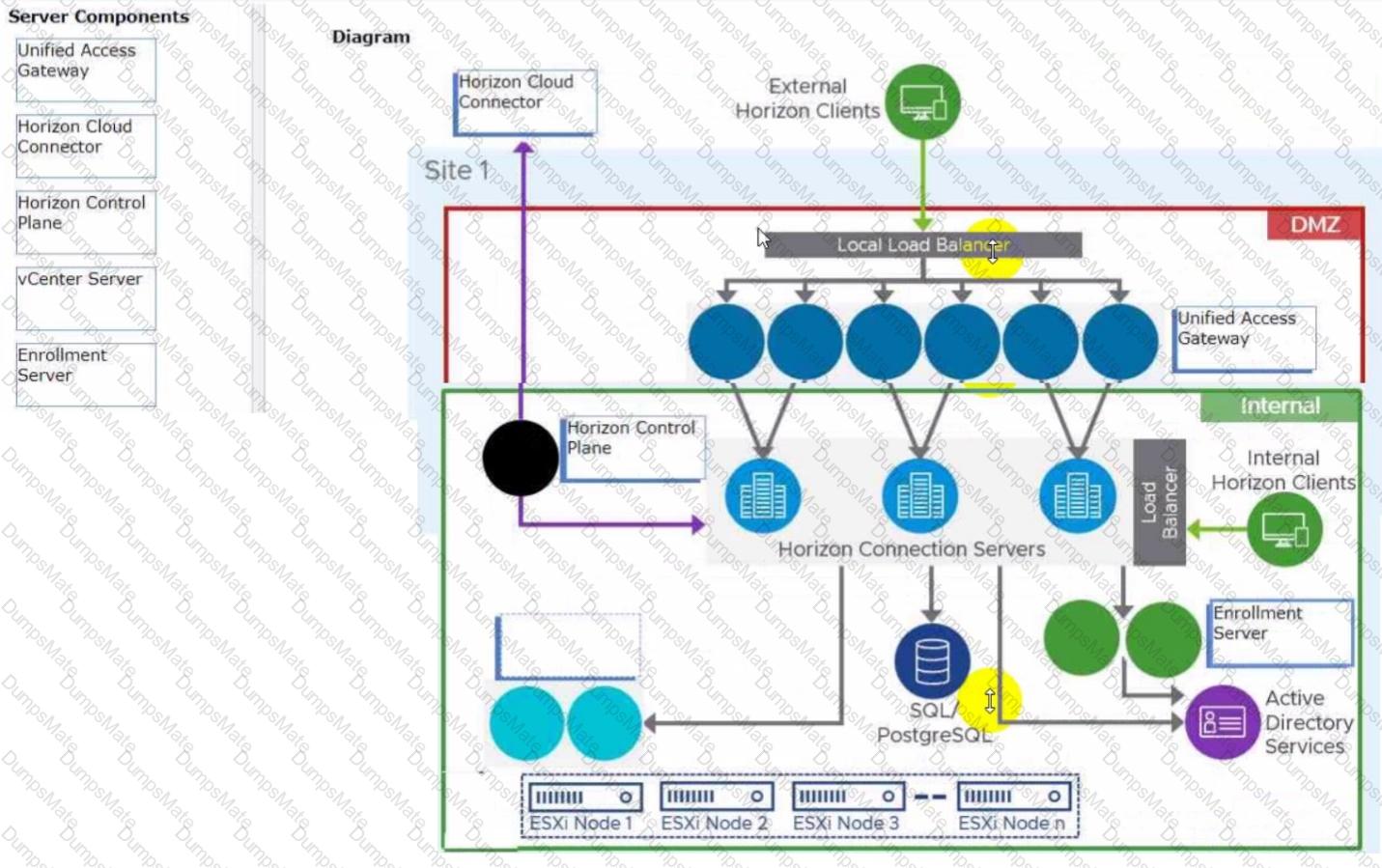
- Load Balancing Across Multiple Pods
- Horizon 7: Monitoring health of Horizon Connection Server using Load Balancer
- [Horizon 7 Pods]
- [Global Settings for Client Sessions in Horizon Console]
- [VMware Horizon Architecture Planning]





 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg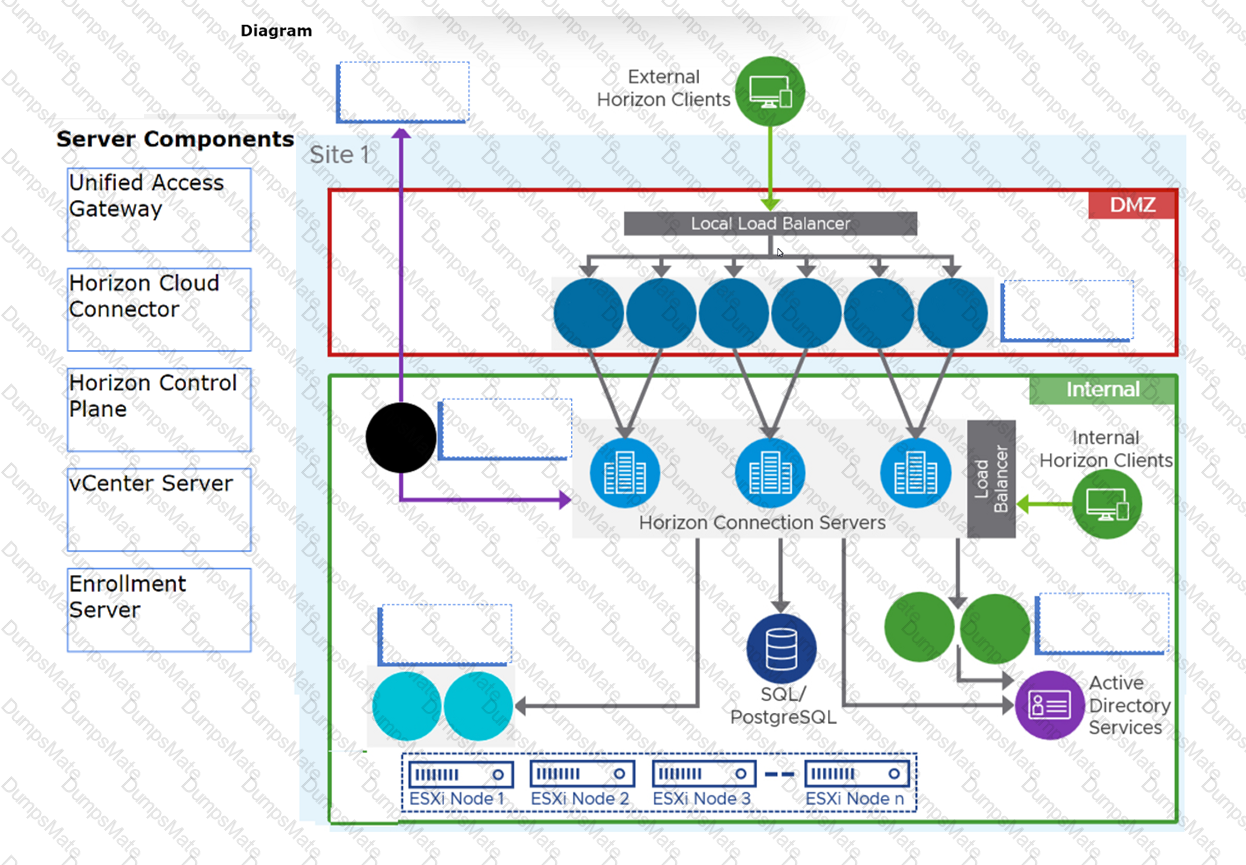




 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg



